Mirai botnet among different instruction sets: x86, ARM, PPC, and MIPS with static analysis
Summary
Mirai
botnet family first discovered in 2016, the botnet will look for devices of IoT
with scanner which embedded a dictionary for brute force attack and
vulnerabilities exploit, and can do a DDoS attack like TCP flood and UDP flood
and so on, later on, the source code distributed in github and different
variants came from that time, nowadays, botnet is big challenging and threat to
IoT, it is worthy doing research with different instruction sets, this report come here for a new try and let’s
do it.
Technical analysis
This
botnet is the ELF for Intel 386 (executable).
The
hash
MD5: 6950F28382D7F11E18BDF53F3983117B
The load segment displays lots of source files that
can help analysts to learn from which source code is being included and infer
the main function of malware, likely with the source file “kill.c” to tell the
analyst it may use the kill command to stop the process and “socket.c,” which
can be used for malware to connect to the network.
Figure1-Source File List
Figure2-Kill
Pid
The botnet at the part of initConnection connects to
the server and port with plain text “31.172.87.248:12345,” and then goes to
sleep and receives the command from the server and starts the attack DDoS
module with processCmd, which supports TCP flood and UDP flood and so on, and
stops the process.
Figure3- InitConnection To Server
Figure4-
ProcessCmd With DDoS
Figure5-The
Type Of ProcessCmd And Stop Process
TCP
flood supports SYN, RST, FIN, ACK and PUSH.
Figure6-TCP
Flood
The getPortz function checks for the existence of
Python, Python3, and Perl binaries. If any exist, it returns."22" If
none exist but /usr/sbin/telnetd is missing, it returns. "Unknown
Port", Otherwise, it defaults to "22".
Figure7-GetPortz
The version of the botnet seems to be focused on
starting an attack with DDoS, not to do cracking with a dictionary for telnet,
and not to use any vulnerability to exploit.
This
botnet is the ELF for ARM (Executable) in 32-bit.
The
hash
MD5: 8ECAFDA00F1F5E5F8E94A10BB94D79B3
The load segment does not display any source files list and the function list without any useful information for analysts; it will take more time to dive deeply into the botnet when doing static analysis.
Figure8-Function Name About
The ELF For ARM
The botnet embedded CVE-2017-17215 vulnerability
exploited Huawei products and used command injection to implant malware, likely
with downloading botnets for expanding the attack surface.
Figure9-
CVE-2017-17215
The
botnet embedded a dictionary to do a brute force attack.
Figure10-A
Dictionary For Brute Force
The botnet kills other processes without plain text
list, linux_eabi_syscallis an assembly-level mechanism for invoking system
calls on ARM architectures, and the number is 37.
Figure11-Kill
Other Process
The
botnet changes the process to hide the real process for the anti-killing virus,
which was running on the victim host.
Figure12-Change
The Real Process
This version of the botnet with ARM architectures seems a bigger challenger than x86 architectures.
This botnet is the ELF for PowerPC (Executable) in 32-bit.
The
hash
MD5: C6F057C974B24F6ABDAC5B76B10040B9
The load segment only displays
“ppc-asm.h” include list and the function list without any useful information
for analysts;
Figure13-Load
Segment
Using
the crontab to execute a task with “bot.conf” file and make the botnet running
as service.
Figure14-
Crontab And Service
The botnet kills other processes without plain text
list, linux_syscall an assembly-level mechanism for invoking system calls
on ARM architectures, and the number is 37.
Figure15-Kill
Other Process
The
botnet changes the process to hide the real process for the anti-killing virus,
which was running on the victim host.
Figure16-
Change The Real Process
This
version of botnet without brute force attack and vulnerability exploited.
This botnet is the ELF for MIPS
(Executable) in 32-bit.
The
hash
MD5: CE6B524DB5612552294B5661EFFED7BD
The load segment does not
display any source files list and the function list without any useful
information for analysts; it will take more time to dive deeply into the botnet
when doing static analysis.
Figure17-Function Name About
The ELF For MIPS
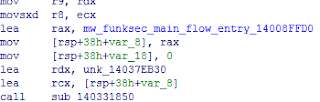
The
entry of variant of MIRAI is still very clearly, the function sub_40BA5C is
main routing.
Figure18-The
Entry
A
dictionary is embedded for brute force in MIPS architectures like the following.
Figure19-
Brute Force
In
MIPS, the number of system calls begins at 4000, and “__asm { syscall }” is an inline
assembly instruction that invokes a system call, the number 4170 is short for
socket connection.
Figure20-Snippet
For Connect
Username and password had been obfuscated with XOR,
and the key was 0x37.
Figure21-Xor
Algorithm
The IP address “41.216.189.127” is a fake IP, which
will be changed by the sub_413780 function in order to hide the real server.
Figure22-
sub_413780 Change Fade IP Address
The new variant uses double obfuscation to encode
strings; it makes analysis more challenging. Maybe it will appear with multiple
obfuscation techniques for anti-analysis.
Figure23-Double
obfuscation
Obviously, the variant of Mirai botnet in MIPS
architectures to do static analysis is a big challenge because of its policy of
obfuscation.
ICOs
6950F28382D7F11E18BDF53F3983117B
8ECAFDA00F1F5E5F8E94A10BB94D79B3
C6F057C974B24F6ABDAC5B76B10040B9
CE6B524DB5612552294B5661EFFED7BD
Conclusion
From the above static analysis, we can get very
limited knowledge about the Mirai botnet with different architectures, especially
since they are a big challenge by obfuscation technique, although we can find
the main routing or basic structure of botnet to go forward, but it still takes
us more time and energy for the whole process of analysis.
End.