Static Analysis of Turla’s Uroboros: Revealing Core Tactics and Technical Mindset
Though
over a decade old, Uroboros reflects a level of technical mastery and creative
mindset that still challenges analysts today
“To understand the
immeasurable, the mind must be extraordinarily quiet, still.”
— Jiddu Krishnamurti
By Seeker(李标明) China
Independent Malware Analyst & Researcher
Download the Full Report (PDF)
Prologue: The Temple and the Kernel
Recently, I still
climbed a mountain and visited the temple again and again. Here, I keep moving
to find more. In fact, to be honest, I’m still facing a lot of unknowns to
learn, and that means continuing even
when I’m confused or overwhelmed. And I like to do internal
observation as my daily habit.
Most call it snake and
Uroburos. I notice that Kaspersky used Uroburos or Uroboros in 2014 or 2015,
but I like the name "Uroboros." Yeah, they are the same thing.
In this report, the
first important thing is to do a simple static analysis and grasp their
mindset.
Sample choice: Uroboros
Yeah,
it’s still the nation-state group APT called Turla.
Sample md5: ed785bbd156b61553aaf78b6f71fb37b
First impression: sophisticated and mastery
The first impression of
Uroboros is very sophisticated; it’s not just binary, it is the design and
thinking. They create a new path but become a part of the operating system,
which is subtle and hides intent inside the design. The very long and deep
execution chain and injection of design from user mode to kernel mode is top
elite level, which implies Turla's understanding of the kernel is amazing. They
understand, they create, and they hide.
Static analysis
Kernel
escalation and monitor the new process created
The malware Uroboros from the application in user mode to kernel mode is a very long execution chain design and complex. From the DriverEntry to the function sub_16B78, alongside the primary path forward, and finally it uses PsSetCreateProcessNotifyRoutine to register NotifyRoutine for kernel callbacks; from there, the key point is to inject the whole design and hijack the new process created.
Fig.1 PsSetCreateProcessNotifyRoutine
and kernel callback
Multi-stage
injection of trusted processes
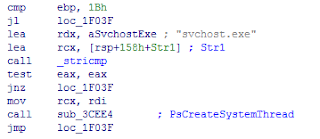
The malware Uroboros uses ZwQuerySystemInformation to enumerate processes, find services such as service.exe, svchost.exe, and browsers (iexplore/firefox/chrome), and determine which is the best place to inject or hide by privilege. The persistence is multi-staged and injected into trusted processes. To intercept, the browser can get the private information to further expand their attack surface.
Fig.2 Inject into
svchost.exe by privilege
Network
persistence and evade detection
The malware Uroboros abused legitimate Windows drivers to hijack system functionality. It modifies kernel function pointers (e.g., in ndis.sys or fwpkclnt.sys) to redirect execution to the same malicious function, sub_4AFBC. ndis.sys handles network traffic, and fwpkclnt.sys is part of the Windows Firewall; pathing them is ideal for stealthy network filtering and intercepting packets. It is a kernel-level network interception technique to maintain persistence and evade detection.
Fig.3 patching the
driver fwpkclnt.sys
Customized
http protocol design thinking
in the function sub_3F23C, From the HTTP request parsing with a specific “type” (==6) and the code comparison with the strings “&a” and the XOR description routine, it is a typical XOR loop, using a static decryption table (unk_65D70). The input (e.g., from &a=) is probably encrypted, and this routine decrypts it. In total, Turla typically uses customized HTTP designed to blend in with Internet traffic.
Fig.4 customized HTTP
protocol
This static analysis reveals that Turla’s Uroboros
rootkit employs kernel-level privilege escalation and monitors process creation
to enable multi-stage injection into trusted system processes. It maintains
network persistence through stealthy communications and evades detection with a
custom-designed HTTP protocol, reflecting a strategic focus on covert, long-term
control and adaptability.
It’s related only to
some primary but limited characteristics. I did not pursue full tracing of all
in this report, to be honest. It’s not a binary but architecture and subversive
thinking. It’s a very exciting and challenging journey.
I hold deep respect for
Turla — not only for their exceptional mastery of Windows kernel internals but
also for the boldness and creativity shown in their techniques. What’s truly
remarkable is that this mindset and technical capability were already present
over a decade ago. It reminds me to stay humble, keep studying and seeking.
Epilogue: What the Kernel Taught Me
The kernel is a deep
ocean and dynamically changing—to keep learning and seeking.
“Do or
do not, there is no try.”
— Master
Yoda
End of Report
Labels: #CoreTactics, #kernel, #rootkit, #TechnicalMindset, #Turla, #Uroboros







0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home