FunkSec Ransomware and Rust Reverse Analysis
Summary
From
the checkpoint
research, the FunkSec ransomware group first emerged publicly in late 2024
and rapidly gained prominence by publishing over 85 claimed victims—more than
any other ransomware group in the month of December. I did research with a
shared sample.
Technical Analysis
FunkSec
Ransomware is named by the binary inside strings “funksec.pdb,” its extension
“.funksec,” and ransom note, written in the Rust computer language and run on
Windows and compiled in the environment of “C:\\Users\\Abdellah\\.cargo\\...,”
with the time date stamp “2024-12-31 20:26:29,” AMD64 Architecture, without a
packer. And "This program requires administrator privileges."
Figure1-Binary Information
Figure2-Ransomware Note Snippet
Like
the other ransom group, it generated a special readme file as a ransom note to
tell the victim about “stop” and “what happened,” including what the bitcoin
wallet address is, how to buy bitcoin, how much bitcoin to pay, and the contact
ID. The special thing is about the “estimated time for data recovery.” A lot of
malware samples I did research on, and I had found this tip; it gives the good
feeling for their professional and advanced group, and don’t forget to tell
people “who they are” as AD. In addition to supporting three onion websites to
visit.
Figure3-Ransomware Note
Snippet
FunkSec
ransomware supports downloading remote JPEG images to change wallpaper from the
URL “https[:]//i.imgur.com/HCYQoVR.jpeg.”This link can still be accessed and
downloaded until “2025/1/22.” The JPG image has the following words.
Firgure4-Wallpaper
The
binary first tries to use “net session” to check whether it can elevate
privileges (the net session command
requires administrative privileges to run successfully); if not, it will
attempt to use the PowerShell command “Start-Process” to launch itself with
elevated privileges.
Figure5-
Net session and Start-Process
FunkSec
ransomware encrypted the file and deleted the original file.
Figure6-Tip
for “Encrypted and deleted file”
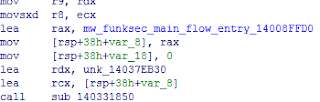
Figure7-The
Entry Of Main Control Flow
One
of the main control flows is as follows.
1.
To create a README file that is the ransomware note.
2.
To use “net session” to check whether it can elevate privileges
3.
To download an image from the website address to change wallpaper
4.
To try to run with administrator privileges
5.
To get USERPROFILE
6. To encrypt and delete a file (ignore attention to encryption methods).
IOCs
2456fdd65bc48203815f22e444d78fb0
https[:]//i.imgur.com/HCYQoVR.jpeg
108[.]160[.]163[.]117
Threat Intelligence
Bitcoin
wallet address:
bc1qrghnt6cqdsxt0qmlcaq0wcavq6pmfm82vtxfeq
Decryptor
file fee: 0.1 BTC
Three
onion websites:
funkiydk7c6j3vvck5zk2giml2u746fa5irwalw2kjem6tvofji7rwid.onion
funknqn44slwmgwgnewne6bintbooauwkaupik4yrlgtycew3ergraid.onion
funkxxkovrk7ctnggbjnthdajav4ggex53k6m2x3esjwlxrkb3qiztid.onion
ransomware note:
End.
Labels: FunkSec, ransomware, Rust Reverse










0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home