The North Korean nation-state APT43 Kimsuky used the PowerShell forceCopy to conduct spear-phishing analysis
Summary
From the AhnLab SEcurity intelligence
Center (ASEC) I noted that Theft of Web Browser Information (forceCopy)
which malware are PowerShell scripts, and I have collected three malwares, they
have similar design, I choose one of them to analysis. The design of the
PowerShell script used by obfuscation technology from Kimsuky is worthy of more
attention, especially nowadays as AI is developing fast; it makes malware
makers and analysts more easily able to do their jobs.
Technical analysis
This
forceCopy is the PowerShell
(executable).
The
hash MD5: 1e9d94d88fdac3c4a0a47a3a1d07e329
The source code is difficult to read, so I did it manually and made it easy to read. These codes are a small part of them.
1. It defines a function (stored in the variable $mqtz60) that takes an array of strings ($vvv32) as input;
2. For each string in the array, it decodes the string from Base64, converts the resulting byte array to a string and then executes the resulting string as PowerShell code.
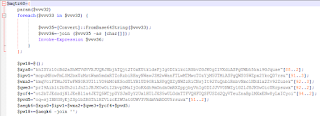
3.The variable $xya0 and it long string and The range [88..2] means it takes characters from index 88 to index 2 in reverse order , This is unusual and likely part of the obfuscation.4. And the other variables $ipv1, $wxa2, $qwe3, $ycf4, $pvd5 are similar, the variable $aegk6 connects with them. Figure1-source code Optimized in format
Just
using “Write-Output” to print the decoded string instead of executing it, and
finally we can get the decrypted source code. This PowerShell script snippet
performs several operations, including interacting with Google Drive, executing
a PowerShell script, and handling output and uploading it with an access
token.
Figure2- decrypted strings
Of course, normally here to change the code to get tmps4.ps1, but I had not found it. Maybe it plans to run a keylogger or other malware to steal victim information. The access token is embedded inside PowerShell, including the other parameters like folderId, clientId, and secret.
Figure3-token
paramers
IOCs
(Md5)
1e9d94d88fdac3c4a0a47a3a1d07e329
Conclusion
The
Kimsuky threat group is continuously updating malware and launching spear
phishing attacks against their targets. It is so hot for their campaign and
also is a huge threat to the economic world.
End.
Labels: #forceCopy, #Kimsuky, #Powershell, #spear-phishing





0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home